Quantum key distribution system against the probabilistic faint after-gate attack
|
Quantum key distribution system against the probabilistic faint after-gate attack |
| Meng Ye,Jian-Hui Li,Yong Wang,Peng Gao,Xin-Xin Lu,Yong-Jun Qian |
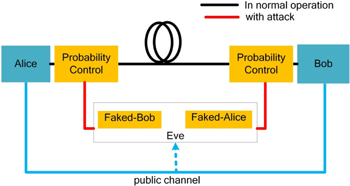
| Figure 1. Schematic of the probabilistic faint after-gate attack. Alice and Bob are legitimate communicate parties. For Alice, Eve is the role of Faked-Bob. For Bob, Eve plays the role of Faked-Alice. Probability control is the module that controls the Eve’s frequency of attack. |

|