Quantum key distribution system against the probabilistic faint after-gate attack
|
Quantum key distribution system against the probabilistic faint after-gate attack |
| Meng Ye,Jian-Hui Li,Yong Wang,Peng Gao,Xin-Xin Lu,Yong-Jun Qian |
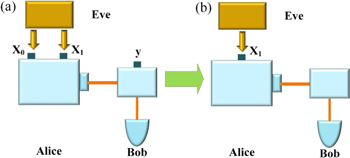
| Figure 2. (a) Weak randomness model, there are two random input bits X 0 and X 1 at Alice’s side. At Bob’s side, there is one random input bit y, where X 0 refers the random input bits to the selection of classical encoding bit, X 1 refers the random input bits to the selection of preparation bases at Alice’s side, y refers to the random input bits to the selection of measurement bases at Bob’s side. (b) Weak randomness model of probabilistic faint after-gate attack, Eve plants hidden variable λ 1 into Alice’s side to control X 1, where X 1 refers the random input bits to the selection of preparation bases at Alice’s side. |

|