Cascading attack on trusted-relay quantum key distribution networks
|
Cascading attack on trusted-relay quantum key distribution networks |
| Jian Wang,Xing-tong Liu |
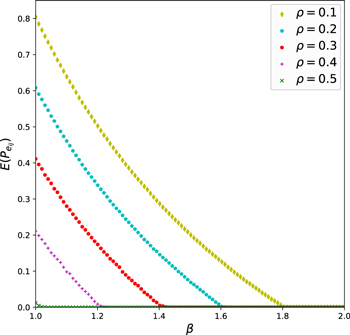
| Figure 4. Influence of ρ on $E(P({e}_{{ij}}))$ in the simulation of a cascading attack on a QKD network. |

|